What Is a Crypto Nonce? Definition, Function, and In-Depth Analysis of Its Applications in Blockchain
1. Basic Definition and Core Concepts of Nonce
Nonce is an abbreviation for “Number used once”. In cryptography and communication protocols, it refers to a random or pseudo-random number generated to guarantee the uniqueness of communications. The nonce’s core attributes include:
• Uniqueness: As the term suggests, this number is used only once within a specific encrypted communication and is never reused.
• Unpredictability: In cryptographic contexts, the nonce must be random to prevent attackers from anticipating its value.
In Bitcoin’s Proof of Work (PoW) mechanism, the nonce is the only variable miners can manually adjust during hash calculations. Miners cannot alter transaction data; they must continually try different nonce values, recalculating the hash each time. When a miner discovers a nonce that produces a block hash meeting the required difficulty, that nonce serves as the proof of work.
This process is similar to buying lottery tickets. The block data represents your name, and the nonce is the random number you select. You keep changing the number (nonce) until you win (meet the hash difficulty).
In Ethereum, the nonce serves two main purposes, with the account nonce being the most common:
- Account Nonce: Every Ethereum account maintains a transaction counter that starts at 0.
- Order Enforcement: Miners must process transactions in nonce order. If you send two transactions with nonce values of 1 and 2, the transaction with nonce 2 will never be executed before the one with nonce 1.
- Double-Spending Prevention: This ensures that the same funds cannot be spent twice due to network delays or other issues.
2. Primary Functions and Value of Nonce
The nonce’s primary purpose is to strengthen system security and integrity:
• Replay Attack Prevention: This is the nonce’s most fundamental function. Attackers may intercept valid communications and attempt to resend them to gain unauthorized access. The nonce ensures that, even if intercepted, the server will reject the request because the number has already expired.
It’s similar to the serial number on a check. If someone cashes a check with number #001, the bank voids that number. Even if someone copies the check, it cannot be cashed again.
• Data Freshness Assurance: By including a nonce, the recipient can verify that the data was generated in real time, not a replay of old information. This prevents attackers from using previous session records to forge identities.
• Enhanced Unpredictability: The nonce introduces a variable into the encryption process, making it much harder for attackers to analyze patterns and compromise the system.
3. Main Types of Nonce
Based on generation method and application needs, nonces are primarily classified into two categories:
• Random Nonce: Generated using a cryptographically secure pseudo-random number generator (CSPRNG), offering high entropy and unpredictability. Commonly used in digital signatures and advanced encryption schemes.
• Sequential Nonce: Produced by incrementing a counter. While less unpredictable, it guarantees absolute uniqueness and is suitable for authentication mechanisms.
4. Multi-Domain Applications of Nonce
Nonce usage spans a wide range of scenarios—from daily web browsing to digital currency transactions, as well as various security protocols and emerging technologies. Its core logic always centers on uniqueness and unpredictability.
• Identity Management and Authentication: In HTTP Digest Authentication, Single Sign-On (SSO), and Two-Factor Authentication (2FA), nonces validate user identity and ensure request authenticity.
• Cryptographic Protocols and Digital Signatures:
◦ During SSL/TLS handshakes, clients and servers exchange nonces to verify identities.
◦ In algorithms like AES-GCM, the nonce functions as the Initialization Vector (IV), ensuring identical plaintexts do not produce identical ciphertexts.
• Blockchain and Distributed Ledger
This is the most prominent application of nonces today, addressing “who gets to record transactions” and “transaction order.”
For example, in Proof of Work (PoW) mining: In Bitcoin, the nonce is a 32-bit field. Miners continuously adjust this number until the block header’s hash is less than the target difficulty.
In Ethereum account management: Each Ethereum account maintains an incrementing nonce. This not only prevents replay attacks (sending the same transaction twice) but also enables users to “replace” or “cancel” stuck transactions by submitting a new transaction with the same nonce and a higher fee.
5. Nonce vs Related Concepts (Nonce vs Hash)
While nonce and hash values frequently appear together in blockchain contexts, they are fundamentally distinct:
A hash value is a “digital fingerprint” of data, determined by the input and fixed in size. A nonce, on the other hand, is a temporary variable used to alter hash outputs.
From a temporal perspective, the hash value serves as a fixed identifier for a dataset, whereas the nonce is typically discarded after a single use.
6. Security Threats and Mitigation for Nonce
If nonce generation or management is flawed, systems face significant risks. Common attacks include:
◦ Nonce Reuse Attack: Attackers exploit reused nonces to break cryptographic protections. For instance, in July 2021, the Anyswap Multichain Router V3 cross-chain protocol signed two transactions with the same value (a signature component), enabling attackers to deduce the private key and resulting in losses of nearly $8 million.
◦ Nonce Prediction Attack: If the nonce generation pattern is predictable, attackers can manipulate mining or authentication processes.
◦ Brute-Force Attack: Attackers exhaustively try nonce values to find a hash that meets the criteria. For example, in 2018, Bitcoin Gold (BTG) suffered multiple 51% attacks. Attackers rented massive computing power to brute-force nonces, ultimately stealing 388,200 BTG and causing losses of about $18 million.
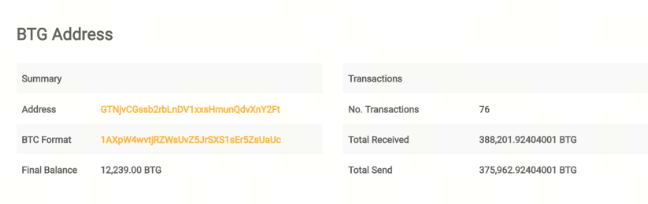
Screenshot source: Bitcoin Gold Explorer
To prevent these attacks, developers and projects should use highly random generation algorithms (such as CSPRNG), enforce strict uniqueness checks, and regularly update cryptographic libraries.
7. Conclusion
As a foundational element of cryptographic technology, the nonce’s “single-use” property provides robust security for complex internet communications and distributed ledgers. Understanding and correctly implementing nonce mechanisms is essential for ensuring the security, transparency, and integrity of the digital world.
Further reading:
Related Articles

In-depth Explanation of Yala: Building a Modular DeFi Yield Aggregator with $YU Stablecoin as a Medium

BTC and Projects in The BRC-20 Ecosystem

What Is a Cold Wallet?

Blockchain Profitability & Issuance - Does It Matter?
What is the Altcoin Season Index?
