He Went Undercover in 600 Scam Groups to Stop Illicit Money Flows
Throughout business history, wherever wealth surges, a struggle between law and order inevitably follows.
Looking back from the end of 2025, global stablecoin issuance has firmly reached $300 billion—nearly triple last year’s figure. Monthly transaction volumes now stand at an astonishing $4 to $5 trillion. Stablecoins have outgrown their “geek toy” reputation, becoming the number one gateway for traditional finance to enter the digital economy.
Beneath this boom, however, lies a darker reality. The latest industry reports estimate that, in 2025, illicit addresses worldwide will receive over $51.3 billion. With hundreds of billions moving across borders in seconds, traditional regulatory tools can’t keep up. It’s nearly impossible to distinguish legitimate transactions from criminal proceeds in real time.
In this world of still-forming rules, Professor Zhou Yajin stands out as a unique entrepreneur.
Zhou Yajin’s career is a textbook example of an elite academic colliding with industry. In 2010, he left for the US to pursue a PhD, spending five years specializing in mobile security. He and his advisor, Professor Jiang Xuxian, then joined Qihoo 360, marking his first leap from the lab to the front lines of business. In 2018, Zhou returned to teach at Zhejiang University.
Three years later, he dove back into the industry and founded the blockchain security firm BlockSec.
Over the past four years, Zhou has led BlockSec through a strategic transformation. The company evolved from smart contract audits into deeper areas like security monitoring, fund tracing, and anti-money laundering (AML) compliance.
Zhou and his team have invested years in specialized on-chain data research. They’ve even used technical means to infiltrate Southeast Asian cybercrime groups, gaining rare insights into their inner workings. Through his perspective, we get a candid look at the real power struggles shaping the digital world.
The following is Zhou Yajin’s personal account, edited by the Beating team after an exclusive interview.
This article is sponsored by Kite AI.
Kite is the first Layer 1 blockchain designed for AI agent payments. This foundational infrastructure enables autonomous AI agents to operate in an environment with verifiable identity, programmable governance, and native stablecoin settlement.
Kite was founded by AI and data infrastructure veterans from Databricks, Uber, and UC Berkeley. The company has raised $35 million from investors including PayPal, General Catalyst, Coinbase Ventures, 8VC, and other top funds.
From Code Audits to the AML Battlefield
I pursued my PhD in the US from 2010 to 2015 under Professor Jiang Xuxian, specializing in mobile security—especially Android malware detection, which was cutting-edge at the time. After graduating in 2015, I joined Qihoo 360 with my advisor to commercialize our research.
In 2018, I joined Zhejiang University, moving back from industry to academia. This coincided with the 2017–2018 ICO boom in China, which brought blockchain into focus for a select few. That’s when I began exploring blockchain security.
I noticed frequent on-chain security incidents back then. Academia had already developed strong solutions, but the industry lagged behind—few paid real attention to these issues.
So, in 2021, Professor Wu Lei and I co-founded BlockSec.
At first, people’s view of a “blockchain security company” was narrow: “Aren’t you just doing audits?” We did begin with smart contract audits.
Our academic background and elite team quickly established us in the audit business. But my vision was broader—I didn’t want the company to just offer security services. Audits address pre-launch risks, but there weren’t good solutions for post-launch protection.
So in 2022, while expanding audits, we began building an on-chain attack monitoring platform. Our product concept was continuous monitoring of on-chain transactions, with the ability to automatically block attack transactions as they occur.
Along the way, we realized that audits and monitoring weren’t enough—projects could still be attacked. Coupled with a rise in phishing, private key loss, and other end-user threats, users kept losing funds. This created new demands.
When projects are hacked or users are phished, they need to file police reports and explain to law enforcement where the money went. Starting in 2022, we launched a fully SaaS-based fund tracing product. Users could subscribe directly—no B2B sales required.
The product’s user base surprised us: not just law enforcement, but journalists, financial institutions, and even many freelance private investigators started using it.
This diverse user base helped us refine the product and attract more customers. Combined with our attack and phishing detection engines, these data tags became our deepest competitive moat.
The turning point came between late 2024 and early 2025.
Stablecoin issuance began to skyrocket. The market was no longer just for crypto natives—many traditional finance professionals entered, and stablecoins were their first digital asset. These users had strong compliance awareness and immediately asked: “If I use stablecoins, how do I address AML and CFT?”
There was a lack of strong compliance solutions, but we had three years of foundational tag data. We quickly launched an AML product. The process was organic: as market needs evolved, we grew from a pure security provider into a comprehensive “security + compliance” vendor.
Undercover
To tackle AML, you must understand exactly how illicit actors use money.
From our research, crypto crime falls into two main categories. The first is “crypto-native”: attacks exploiting DeFi code vulnerabilities, private key theft, or phishing—crimes that wouldn’t exist without blockchain.
The second is “crypto-driven,” such as online scams, extortion, and human trafficking. Crypto has dramatically increased the speed and anonymity of cross-border transfers. The most shocking is human trafficking within Southeast Asia’s online scam industry.
Many see online scams as distant, but the job ads are highly targeted: starting salaries of 19,000 RMB, airfare, meals, and housing included, even promises of “Shenzhen social insurance.” These tactics target those aged 18–37, luring victims across borders into scam compounds in Myanmar, Cambodia, or Laos.

Modern scam compounds are structured like legitimate companies, with dedicated finance, tech, and communications teams. Maintaining such a large operation requires a constant influx of “labor.” But the compounds (buyers) and traffickers (suppliers) don’t know each other and have no trust online.
This gave rise to “labor guarantee platforms”—intermediaries that provide escrow for illegal transactions.
The system works much like Taobao. The compound deposits a USDT bond with the guarantee platform; traffickers deliver victims to designated “inspection” points.
Once both sides confirm delivery in a private Telegram group, the platform releases the bond to the trafficker. The rule is simple: “person delivered, payment released.” If either side defaults, the platform freezes or confiscates the bond to compensate the other party.
To attract clients, these platforms run public Telegram channels to show off. For example, channels like Linghang Guarantee or Haowang Guarantee use bots to post real-time deal screenshots and on-chain transfers. They even run promotions—commission discounts, “buy 10, get 2 free” ads—just like mainstream e-commerce.
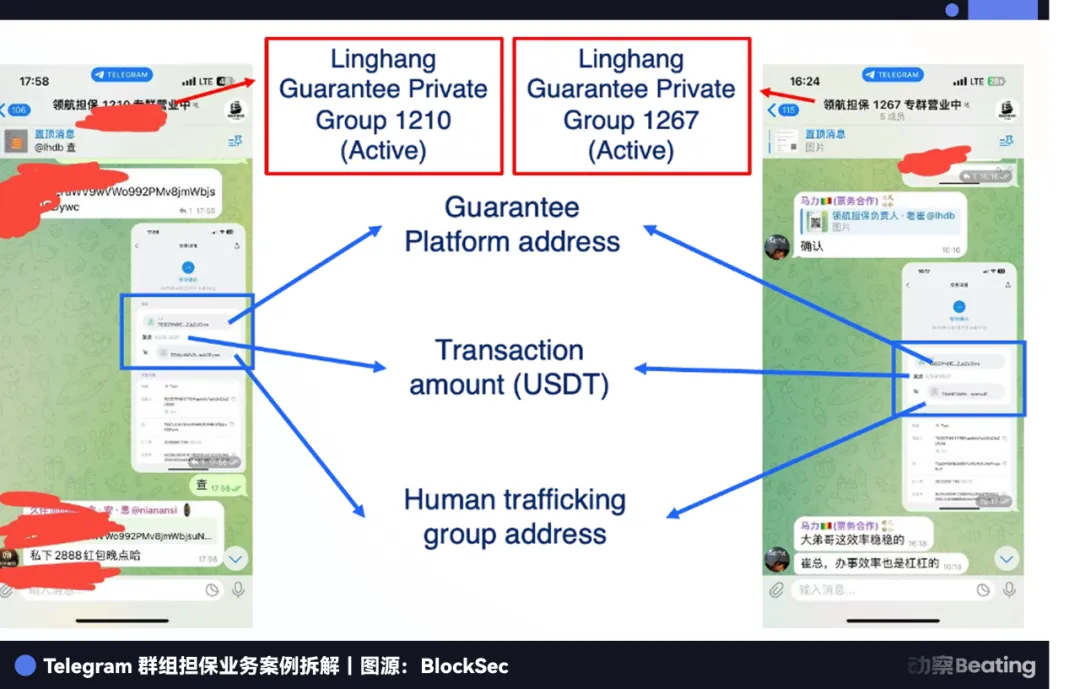
This is our most direct window into the underworld.
From February to August 2025, we built an automated system to continuously infiltrate these groups and capture intelligence. Since the chats are full of jargon, we trained a large language model for analysis.
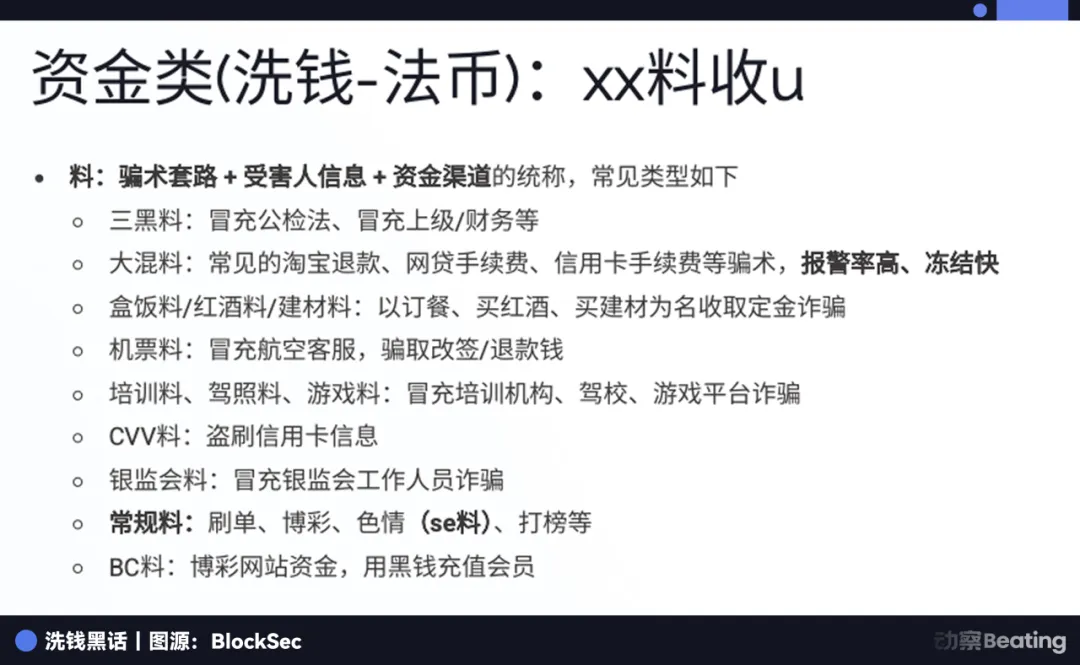
In black market slang, victims are “fish,” while scam tactics and victim info are called “material.” There are “triple black material,” “mixed material,” “ticket material,” and more. For laundering, “first-level material” refers to funds taken directly from victims, while “second-level material” refers to funds laundered through layers.
There’s also a role called “phone port,” where domestic accomplices use audio cables or special apps to relay overseas scam calls through local phones, bypassing anti-fraud blocks and earning around 200 USDT per hour. Many small-town youths are recruited for this work.
Some groups even circulate “anti-police guides,” detailing how to evade investigation—claiming a lost phone, deleting scripts and encrypted apps in advance. The guides end on a bitterly ironic note: “To every hardworking person.”
After six months of automated surveillance, we identified 634 addresses linked to human trafficking groups on a single guarantee platform, tracing nearly $12 million in illicit transactions. At peak, 10 people per day were trafficked through this platform alone. The reality may be worse, as other platforms exist.
When tracing funds, we found that most moved on TRON, mainly using USDT. TRON’s low barriers and fees are ideal for less sophisticated criminal groups. Even as fees have risen, their habits are entrenched.
Analyzing over 120 groups’ fund flows, we found more than 34.9% of illicit funds ended up in OKX hot wallets, 6.9% in Binance, and 14.4% in Huiwang-related hot wallets.
When you can track the origin and flow of these funds, AML becomes more than a slogan. Real, grassroots data is now the core moat for security and compliance.
12 Seconds: Front-Running Hackers in the Mempool
Security professionals have long faced a dilemma: audits only guarantee code safety at launch. Once live, projects are under 24/7 scrutiny from global hackers. If audits are “static defense,” can we create “dynamic interception”?
In 2022, we launched an on-chain attack monitoring platform alongside our audit services. The core idea: monitor Ethereum’s mempool—the “waiting room” where all transactions queue before block inclusion.
There, we track not only ordinary transactions but also those with attack signatures. When a suspicious transaction is detected, our system instantly launches automated analysis in a private chain environment: What’s the intent? Is the logic valid? How much could be stolen?
The most intense battles play out in just 12 seconds.
After Ethereum’s merge, block times fixed at 12 seconds. That means, from the moment a hacker sends an attack command to block confirmation, there’s a razor-thin window. These few seconds are the golden rescue period for white hats.
Once our system confirms an attack, it automatically creates a “front-running” transaction—nearly identical to the hacker’s, but with the recipient address switched to our secure wallet.
To beat the hacker, we must win miners’ priority.
Hackers usually set a standard gas fee to maximize profit. We use algorithms to bid much higher—sometimes even sharing part of the transaction with miners. Driven by profit, miners prioritize our transaction. Once it’s executed, the hacker’s is invalidated.
This capability has saved many projects in real-world attacks.
One classic case: we successfully front-ran an attack in the mempool, recovering 2,909 ETH for a protocol. The hacker had already triggered a vulnerability, with millions at stake. Our monitoring system alerted instantly, and within seconds, we completed attack simulation, transaction generation, and gas bidding. Ultimately, the funds reached our secure address before the hacker could act.
Previously, hacked projects could only beg for help on Twitter or negotiate with hackers for bounties. Now, we can intercept the funds just before the hacker succeeds.
To defend the last line in this “code is law” dark forest, you must outsmart and outrun the hackers.
Epilogue
If the past decade in crypto was a “gold rush,” 2025 marks the return of “certainty.” As stablecoin volumes surge to $300 billion and a digital financial system evolves from “wilderness” to “city-state,” technology is no longer just a tool for wealth—it must first be a shield against the darkness of human nature.
Zhou Yajin and his team’s transformation mirrors this logic. From code audits to dynamic interception, and deep dives into illicit networks, this isn’t lone heroism but the inevitable defense mechanism of technological evolution at scale.
In a world where code is law, if illicit fund flows and failed security are left unchecked, the so-called “financial revolution” will remain a game for the few.
Every industry that reaches the mainstream has endured the painful journey from chaos to rule of law. It’s a long, often tedious process, but as Zhou Yajin says, the ultimate form of security is “invisible.”
Only when security becomes as omnipresent and unnoticed as air will this once-volatile digital frontier truly complete its civilizing transformation.
Statement:
- This article is reprinted from [Beating], with original copyright belonging to [Sleepy.txt]. For reprint concerns, please contact the Gate Learn team for prompt handling.
- Disclaimer: The views and opinions expressed are solely those of the author and do not constitute investment advice.
- Other language versions are translated by the Gate Learn team. Without mentioning Gate, do not copy, distribute, or plagiarize these translations.
Related Articles

The Future of Cross-Chain Bridges: Full-Chain Interoperability Becomes Inevitable, Liquidity Bridges Will Decline

Solana Need L2s And Appchains?

Sui: How are users leveraging its speed, security, & scalability?

Navigating the Zero Knowledge Landscape

What is Tronscan and How Can You Use it in 2025?
